Secrets - HackTM CTF Writeup
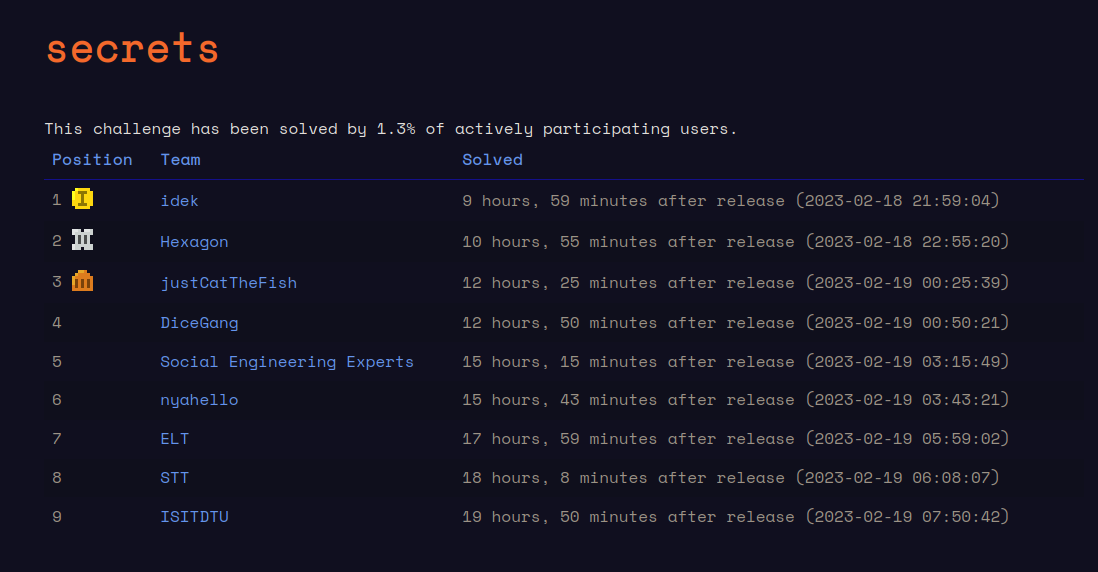
In this article we will solve the final web challenge of the HackTM CTF. The challenge Secrets, is a private note application. We do not have the source code of it.
Here is the preview of the challenge which has been solved only by 9 teams.
TL;DR
The goal was to exfiltrate the note from the bot using an XS-Leaks technique called “Cross-Origin Redirects and CSP Violations”.
Overview
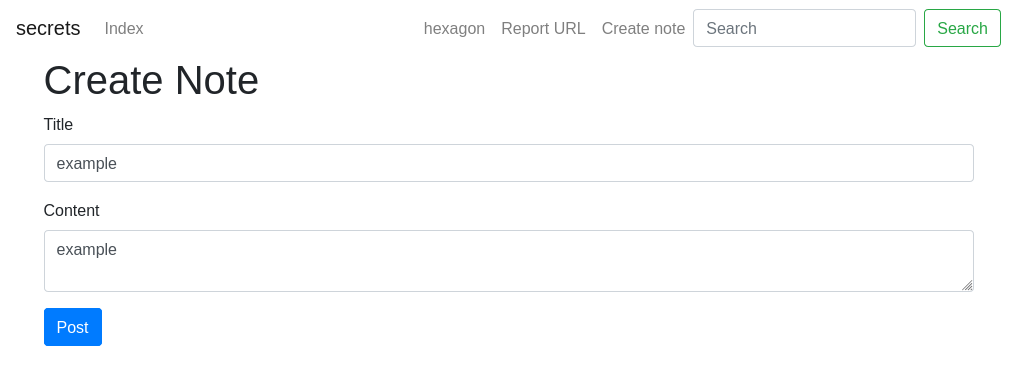
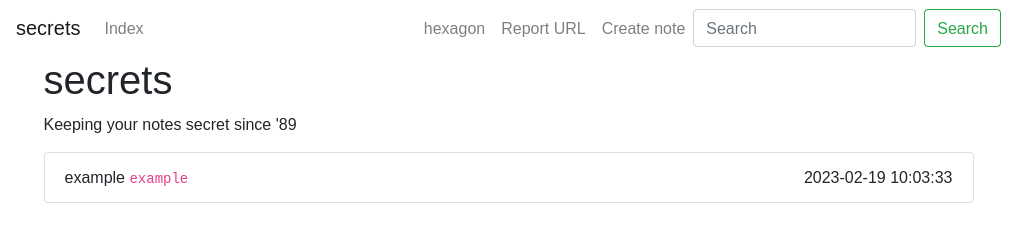
Here is the note application. First, we can register and then log on to the website.

After the login, we notice that the application allows us to:
- Create notes
- Search for our notes
- Report a URL to an admin (bot)
We can create a simple note and view it on the home page:
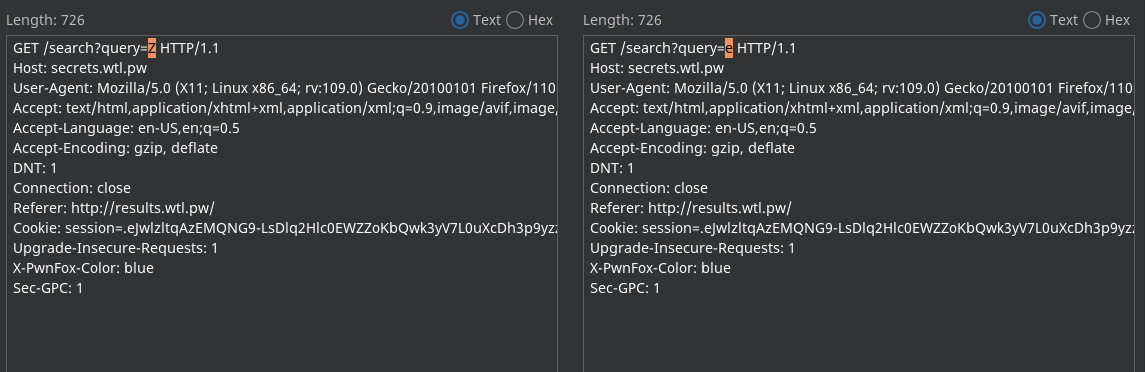
The search functionality has two behaviours depending on the success of the query. Here is an example with a valid and invalid search query on our example note:
- On the right, a valid query because the ’example’ word contains the letter ’e'.
- On the left, an invalid query because the ’example’ word does not contain the letter ‘Z’.
You can use the Burpsuite
Comparertab to reproduce this view.
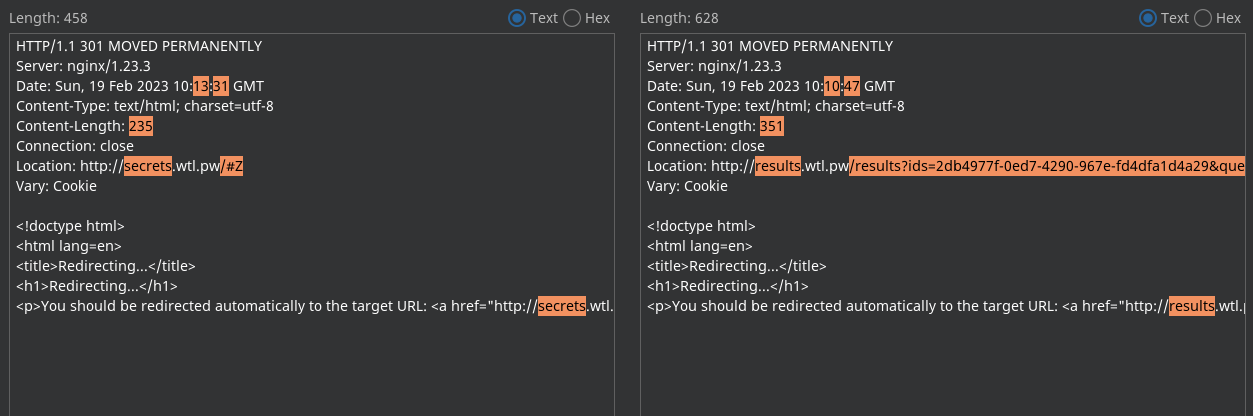
A notable difference in the 2 HTTP responses is that the redirection is not on the same path, and especially, not on the same domain (results.wtl.pw and secrets.wtl.pw).
- Valid query:
http://results.wtl.pw/results?ids=<note_uuid>&query=<query> - Invalid query:
http://secrets.wtl.pw/#<query>
In addition, the attributes of the session cookie are not very secure:
SameSite: None: The cookie will be attached from a request send from every site.Secure: false: The cookie can be used by an HTTP server (no HTTPS requirement).
All these conditions lead us to believe that the goal of the challenge is to exfiltrate the bot’s notes using an XS-Leaks vulnerability.
Cross-site leaks (aka XS-Leaks, XSLeaks) are a class of vulnerabilities derived from side-channels built into the web platform. They take advantage of the web’s core principle of composability, which allows websites to interact with each other, and abuse legitimate mechanisms to infer information about the user. Source xsleaks.dev.
Exploitation
To exfiltrate the flag, we tried to use the following 2 XS-Leaks techniques:
Unfortunately, the first technique only worked on our browsers and not the bot. So we will explore the second one.
The goal of the second technique is to use CSP (Content-Security-Policy) to block one domain on both, results.wtl.pw and secrets.wtl.pw. If the blocked domain is requested by the victim, the Javascript event securitypolicyviolation will be triggered.
We can therefore detect whether a domain has been visited by the bot or not during a search via a form submission by monitoring the form-action CSP directive.
Here is an example:
|
|
To extract the flag more quickly, we used a recursion technique implemented with PHP :
|
|
When testing a search, the form will be sent. In case of success, the bot is redirected with a ?flag= parameter containing the value of the search.
|
|
If our server is reached with the flag parameter, it will start the recursion by opening a window for each new character to test.
|
|
Finally, we send the URL of our server to the bot and wait for the flag.
The flag appears progressively on our server :
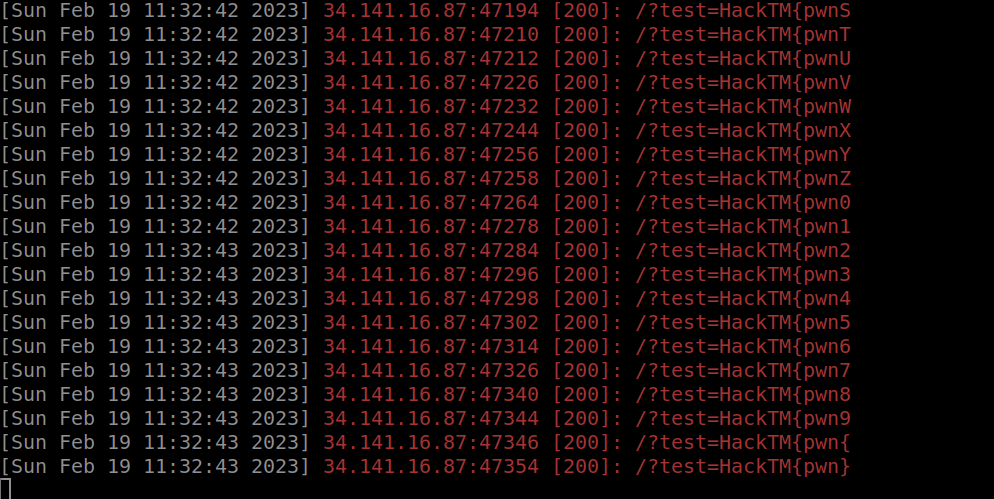
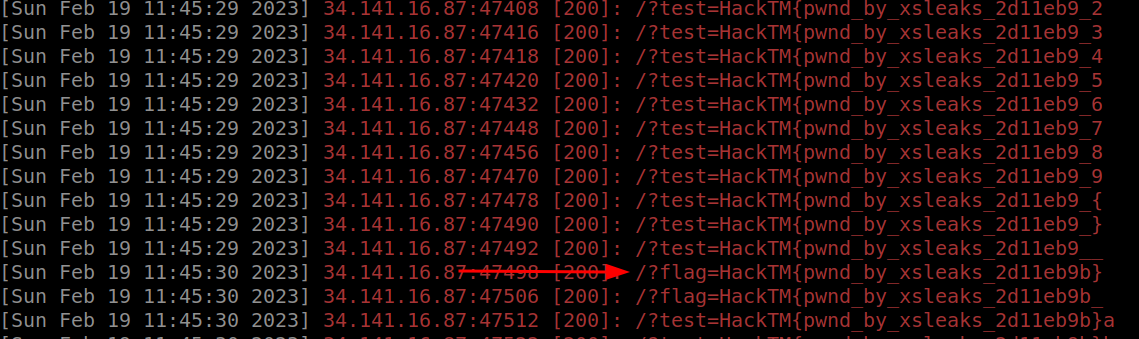
It was a bit complicated to exiltrate the flag as the
_character match every chars.
And we get the flag HackTM{pwnd_by_xsleaks_2d11eb9b} !!!